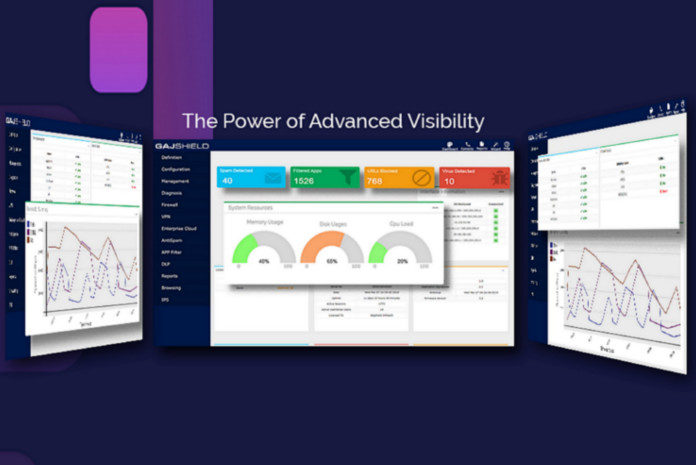
GajShield Infotech has announced the next generation network security solutions, ‘GAJ OS Bulwark 4.0’. Enhancing the firewall experience, backed by contextual intelligence, the Bulwark 4.0 goes beyond just application context and gains visibility at different levels, deeper than any current firewall.
The newly released version 4.0, dubbed ‘Bulwark’ is more powerful and aims to add greater visibility, deeper inspection and better security. The contextual intelligence engine gains a complete visibility on the network traffic to implement better security policies.
The firewall offers a host of security features such as anti-malware, spam-filtering, and contextual intelligence among others. The new version of the firmware comes with a redefined UI and a contextual intelligence engine that filters sensitive content and information from all outgoing traffic, be it through email, file sharing services such as Dropbox and WeTransfer, or social media platforms like Twitter and LinkedIn.
Sonit Jain, CEO, Gajshield Infotech said, “Security is more than just keeping bad actors out of your organizational network and keeping sensitive information within your organization. It also includes having the ability to monitor and control all your IT assets, connections, applications, and communications to identify threat patterns and vulnerabilities. While such visibility has always been a part of Gajshield’s offerings, Bulwark 4.0 takes it to the next level by offering a much more detailed reporting through a highly interactive GUI”
“Bulwark builds on the existing contextual intelligence technology that prevents all sensitive data, in any form, from leaving the secure confines of a business. It determines the context of every instance of outgoing communication by analyzing factors such as the sender, recipient, the body of the message, and even the content within attachments to identify suspicious behavior. It also enables security administrators to fine tune the rules and filters used for stopping the leakage of private information. However, despite the fortified data security measures, we have ensured that authorized users within the organization can still enjoy easy access to the information they need” he further added.